University Laboratories in Tokyo Access Control Management Case Study

Project Description
Project Site: Top-class University in Tokyo
End User: 65 Laboratories of a Top-class University in Tokyo
Our client is a top-class university and is renowned of its outstanding academic and research ability in Tokyo Japan. The institute owns 65 laboratories in total with more than 300 research staffs and professionals, which are mainly for high-end scientific research & development and technological innovations.
These laboratories have been partnered and working closely alongside governmental and commercial organizations, thus contain highly confidential information and high-value unreleased experiment data, and may even be related to national safety.
取引先の要求
Different Access Control Authorities for Different Laboratories
As mentioned, there are as many as 65 laboratories the University owns with different purposes, undergoing projects and research, and academic staffs in charge of. Thus, each laboratory requires a specific authority of access with every staff’s access authority customized.
Multi -Biometric Verification
Conventional verification methods including password and card could hardly verify the authenticity of the password or card holders’ identities. Truly reliable verification method of a person’s identity thus become the critical point of the security. Thus it requires a hybrid biometric verification method with double authentication of a person’s identity.
High Verification Speed
The laboratories are accessed by more than 300 staffs in a single day, research and development works need to be processed with high efficiency. Thus, an access control system that has a high speed of verification becomes ultimately crucial.
Internally Sealed Network Management
The research and development work requires an extremely high confidentiality, any leakage of the information and data could cause serious consequences. Thus, an internally sealed network management is important to prevent possible security risks and threats.
実装ソリューション
Configurations
Access Control Management System
Standalone Access Control and Time & Attendance Terminal with 4-in-1 Fingerprint, Face Recognition, RFID and Password Verifications
MultiBio700
System
Device Name
Device Model
Schematic Diagram
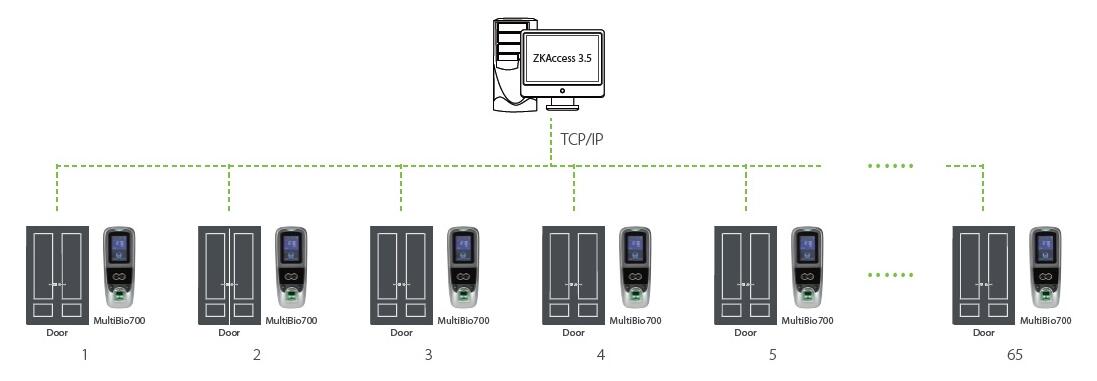
Software
ZKAccess3.5
Technical Features/Solution
• There are 65 laboratories accesses with approximately 300 persons to manage.
• Each access is equipped with a MultiBio700 Standalone Terminal.
• All staffs are biometrically verified by fingerprint or face recognition methods. Some critical accesses requires both fingerprint and face recognition methods to ensure full security.
• Some other critical accesses require 2-person verification. Access is only granted after both staffs have been biometrically verified to prevent fake login.
Function Description
• MultiBio700 is a standalone terminal for both access control and time & attendance. It takes easy installation but provides significantly strong functions, including fingerprint, face recognition, RFID and password verification methods. Its verification speed is less than a second, with large storage space up to 1,500 faces and 2,000 fingerprints.
• Terminals are only managed by ZKAccess3.5 Access Control Software. The entire network is internally sealed.
• ZKAccess3.5 is a customer service based access control software. With highly user friendly UI, it is able to control every door, time zone, staffs with unique access right.
• 20 access rights groups with 15 different time zones have been set up in this project. The access rights and time zones are modifiable by the manager through ZKAccess3.5 in any time according to the client’s needs.
• Anti-passback function prevents any tail-gating access.
• The client is very satisfied with how the machines and software work since it significantly enhances the entire security level of the institute with user friendly management.





 タッチレス認証
タッチレス認証 アクセス制御
アクセス制御 グリーンラベル
グリーンラベル 生体認証スキャナー
生体認証スキャナー 入口制御
入口制御 セキュリティチェック
セキュリティチェック